The tests team starts the actual attack. Pen testers might attempt a number of attacks dependant upon the target program, the vulnerabilities they observed, along with the scope on the examination. Several of the most often examined attacks involve:Cybersecurity consulting services Remodel your enterprise and control danger with a global field chie
 Tony Danza Then & Now!
Tony Danza Then & Now! Kelly McGillis Then & Now!
Kelly McGillis Then & Now!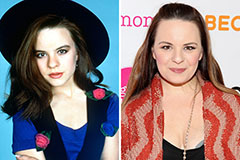 Jenna Von Oy Then & Now!
Jenna Von Oy Then & Now!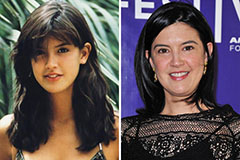 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Rachael Leigh Cook Then & Now!
Rachael Leigh Cook Then & Now!